Business continuity
Day-to-day protection, in addition to disaster recovery
Planning business continuity and disaster recovery processes for an event like a fire may seem so unlikely that it is difficult to give the job priority amongst the day-to-day pressures of running a business. Understanding how business-continuity planning offers protection, advantages and savings on a day-to-day basis, as well as after a serious disaster, may help get the job done.
At IT Basecamp the tech team supports clients with business continuity issues daily via the IT Basecamp help desk. The vast majority of these support tickets surround user issues involving accidentally deleted data - overwriting files or deleting shared folders, for example. For clients who have business continuity plans in place, data is quickly recovered and restored. For those without the correct planning, the result can be very different - hours of downtime for staff and loss of critical business data like client history and contact details, invoicing or payroll.
Having the correct systems in place to continue business with little or no downtime and stress is the essence of business continuity planning. If a company’s essential services are unavailable, the ongoing cost of downtime and lost productivity is crippling. Knowing what your recovery objectives are forms the basis of a recovery plan. From an IT perspective, here are the main areas to factor into a business continuity and disaster recovery plan:
Antivirus and firewalls
A common question from business owners: why do I need both anti-virus software AND a firewall?
The two are different, equally important aspects of network security. A firewall operates at the network level and acts as a gatekeeper, preventing unauthorised access to the network. Anti-virus or anti-malware software works at the device level to detect and remove viruses and malware. While it might appear tempting to economise by running just one or the other, it’s a false economy that leaves significant holes in network security. The cost of cleaning up the damage caused by malware is likely to far exceed the cost of being properly protected.
While a firewall solution does incorporate anti-virus, it only acts at the gateway point of the network. So, for example, employees inserting a USB into their computer or using tethering or hotspotting to work remotely will inadvertently side-step any protection provided by the network firewall. Conversely, a firewall protects devices other than PCs, such as Wi-Fi access points and peripheral devices like printers. In addition, firewalls provide other features including device management, anti-spam and web filtering.
IT Basecamp is an authorised Fortinet products reseller and offers the Fortinet UTM (Unified Threat Management) bundle for firewall security. At the anti-virus level we offer Kaspersky or Trend Micro solutions, depending on the client’s requirements.
Backups
Having a backup solution is more than simply backing up server data. It’s necessary to capture the whole server environment, plus files and folders, and then knowing how to retrieve it. This is the disaster recovery aspect of the planning - yes the data is recoverable; the second step to consider is how to keep the business running through a fault. A cloud solution can offer a fast restore option for an on-premise network - a temporary virtual server in the cloud can be quickly configured so your business can operate while physical hardware is replaced or, in extreme circumstances, new premises are located.
For companies operating cloud and data centre network solutions, access is re-routed as soon as alerts identify a fault - and issues are often fixed before a client notices the outage.
IT Basecamp offers three technologies for backup solutions - VEEAM, Acronis and Datto. With expertise in each of these, the tech team is well-positioned to advise on the best solution for a client’s circumstances.
All backup solutions with IT Basecamp include backup monitoring and fault resolution. Even backups can fail. Reporting is built-in and each day the tech team checks logs to make sure client backups are running and current to ensure that, if ever needed, the correct data is available.
Cybercrime/scams
Cybercrime and scams are an issue that all businesses need to be aware of. Hackers and scammers now regularly attack small businesses - cybercrime is no longer a threat only posed to large corporations and it is costing Australian businesses millions a year. The Australian Competition and Consumer Commission reports that business email compromise (BEC) scams rose by 30% and cost Australian businesses $2.8 million in 2018.
Email scams occur when the hacker gains access to the corporate email account and either impersonates the company to clients or impersonates management within the business. In either circumstance, the hacker's goal is to divert company funds internally or invoice payments from customers.
Protecting a business from this sort of attack and ensuring business continuity is twofold - from a technical perspective two-factor authentication is a must. Using this process a user's claimed identity is confirmed by using a password (something they know) and a second factor, a code, that is sent to them in real-time through a device like their phone. Using two-factor authentication instantly protects against users applying passwords that are not strong enough - the most common weakness in email security.
The second aspect of protecting against cybercrime is awareness and education. Stay in touch with the Australian Competition and Consumer Commission's Scamwatch website and keep abreast of the scams currently in use. Ensure employees know of the scams too - awareness of what a scam might look like is invaluable when it comes to identifying suspicious activity.
Virtualisation
With relation to business continuity, virtualisation has much to offer. Virtualisation can be applied to all parts of IT infrastructure and used to achieve 100% redundancy and solid disaster recovery procedures. Replicating a corporate network using virtualisation either onsite, in the cloud or in a data centre means backups are always ready and available fast, in the event of a fault or disaster.
Warranty and licence tracking, expiry and renewals
One of the more mundane aspects of business continuity is managing warranties and subscriptions. However, mundane or not, losing track of such details can cause business disruptions as easily as any hardware failure. Imagine a website that goes offline or corporate email stops working, simply because a renewal has been missed. IT Basecamp offers systems to record client warranty and licencing details and notify you in advance of when your licences need renewing.
RMM - remote monitoring and management
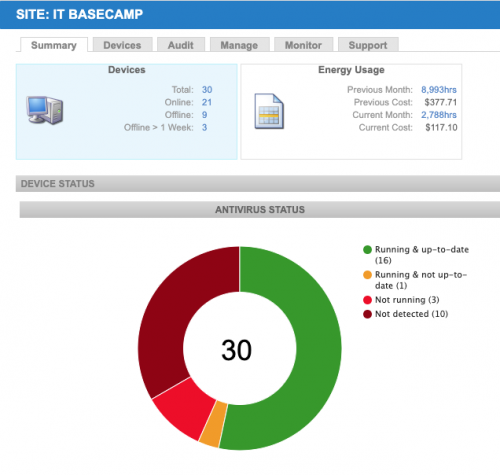
Remote monitoring and management (RMM) is a proactive business continuity technique. Rather than planning a course of action if a certain scenario should arise, RMM is about preventing issues. With IT Basecamp’s RMM offering a company’s servers and workstations can be continually monitored for problems. Remote monitoring can detect:
- if a device’s software is up-to-date,
- corruption in the operating system,
- if a device’s disk space is approaching its limit,
- if the device is down.
With RMM mass deployment of updates can be achieved, running scripts to update machines or changing firewall settings as necessary. At $5 per workstation per month, it is a valuable investment for peace of mind.